Email Protection with Inky
Mosaic with the help of Inky help companies secure email on a cloud platform. We will instantly scans inbound, internal, and outbound emails to eliminate phishing, account takeover, and data leaks.
Common Security Threats
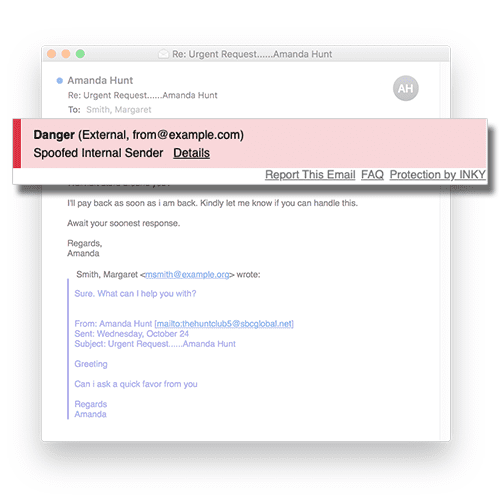
Sender Impersonation
Sender Impersonation is a clever attack where impostors either act under the identities of internal employees (oftentimes the CEO!) for financial gain. In a majority of cases, impersonation attempts occur with attackers emailing company employees from a fraudulent domain name that’s very close to the company’s domain. Usually, the criminal has used social engineering tactics to understand the business structure of an organization and coerced the employee into a financial transfer.
Brand Forgery
Brand forgery emails look like a legitimate email from a brand you know and trust– but it’s not really from that brand. Through good marketing, many companies have trained people to associate certain images or phrases with a given brand. Brand recognition helps sell products, but it also leaves users vulnerable to brand forgery attacks. By including branding from companies that users trust, phishers can make their emails look more authentic and trustworthy to their targets. As these phishing schemes become more sophisticated, INKY’s advanced brand forgery detection plays an increasingly important role in phishing protection.
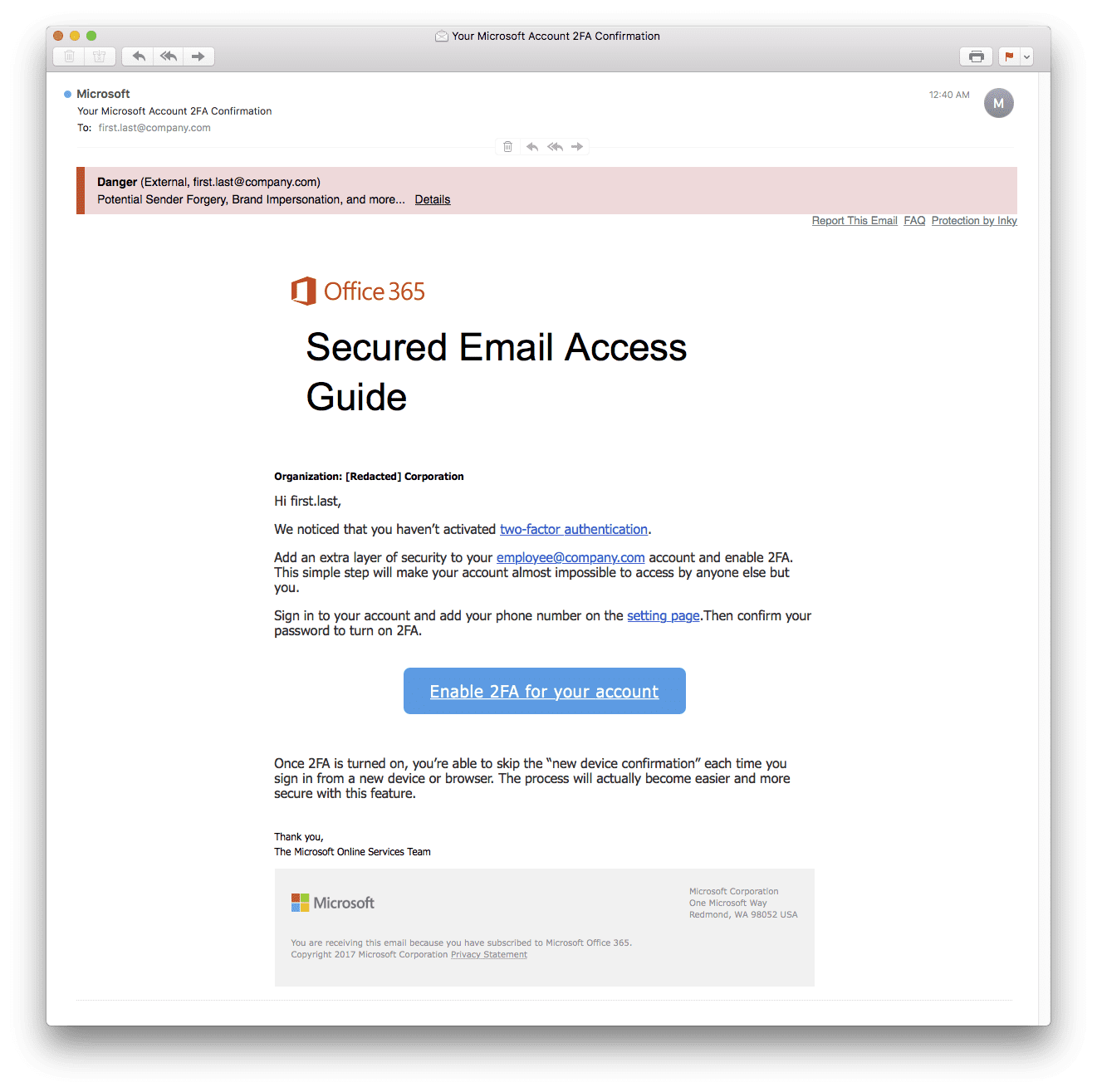
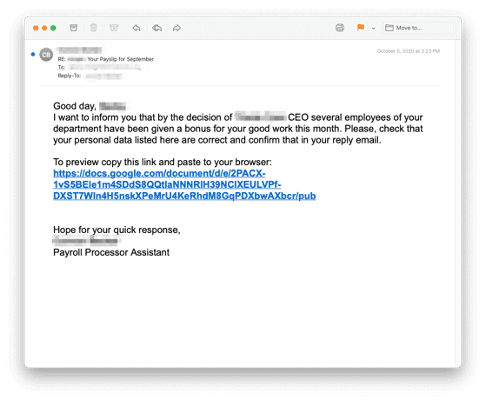
Ransomware and Malware
A particularly destructive tool hackers use to attack their targets is email that contains unsuspecting links or attachments to malware. They design phishing emails that set the recipient up for what is called ‘malware injection’. From there, the malware performs any number of tasks, including spreading itself throughout the network, data exfiltration, surveillance, and business disruption.

Sender Impersonation
Sender Impersonation is a clever attack where impostors either act under the identities of internal employees (oftentimes the CEO!) for financial gain. In a majority of cases, impersonation attempts occur with attackers emailing company employees from a fraudulent domain name that’s very close to the company’s domain. Usually, the criminal has used social engineering tactics to understand the business structure of an organization and coerced the employee into a financial transfer.
Our Platform with Inky
What Makes INKY More Effective?
Today’s criminals employ a variety of incredibly sophisticated techniques that elude even the most skeptical and well-trained eyes. This is where INKY excels. Through innovative use of computer vision, AI, and machine learning INKY catches everything.



